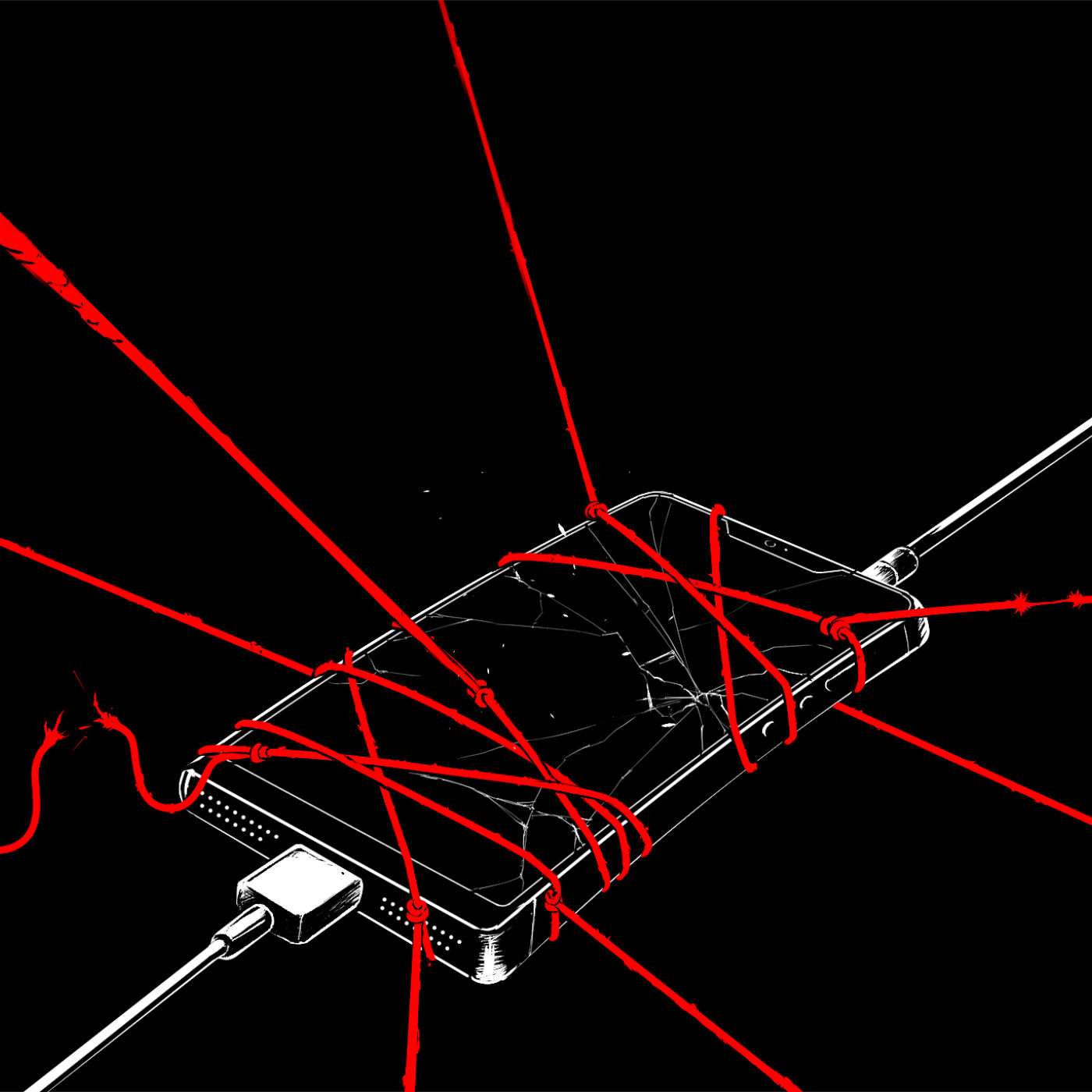
Deep Dive
- Weeping Angel records audio from Samsung smart TVs in 'fake off' mode.
- The CIA uses this to gather intelligence without leaving behind physical bugs.
- The TV appears off but continues to record audio, which can be retrieved later.
Shownotes Transcript
So I was looking through wick likes other day as one does, right? And I came across something that I ve found rather fascinating. There's a thing that the CIA develops called weeping Angel.
So you have a samsung smart T. V. There's a really odd feature in IT is called fake off.
And when the T V is on, you can push, mute, one, a, two, then power. And the T V appears to turn off. But IT doesn't.
Now, these smart tvs often have a microphone belt in, so you can give them voice commands. And when the T V is off, the mike isn't listening. But when the T V is in fake off, the mike is still active.
So what the CIA did was they develop some kind of spyware for the samsung smart T, V. Or IT would record the audio from the mike and store IT on the T V. So I imagine a scenario is that A C I age and would want to plan a listening device and someone's bedroom and goes in, but then sees, oh, they've got a samsung smart T.
V, which is already a listening device, no need leave behind a bug that I could discovered. Let's just live off the land as they say. So the C I age and uploads the spire onto the T, V, and then puts the T, V in fake off mode and leaves and the TV sits there recording all the audio in the room, but appears to be off.
And then the CIA agent can remotely connect back to the T, V, and get the audio files, or come back into the room later and retrieve them off the T, V. It's wild. What Spiker is developed by the federal authorities isn't IT.
These are true stories from the dark side of the internet. I'm jack ryder. This is dark net dies.
This episode is sponsored by a threat locker. Ransom supply chain in attacks and zero day exploit es can strike without warning, leaving your businesses sensitive data and digital assets vulnerable. But imagine a world where your cyber security strategy could prevent these threats, that the power of threat locker, zero trust and point protection platform, robust cyber security, is a non negotiable to safeguard organizations from cyberattacks.
Threat locker implements a proactive, denied by default approach to cy security, blocking every action process and user, unless specifically by your team. This least privilege strategy mitigates the explanation of trusted applications and ensures twenty four, seven, three, sixty five protection of your organization. The core of threat locker is its protect to sweet, including application allow, listing, ring fencing and network rol. Additional tools like the threat locker detect E D R, storage control, elevation control and configuration manager enhancer cybersecurity posture, and streamline internal I T and security Operations to learn more about how threat locker can help mitigate unknown threats in your digital environment and allowing your organization with respect and complained frameworks, visit threat locker dot com. That's threat locker dot com.
This episode is sponsored by spy cloud with major breaches in cyber attacks. Making the news daily taking action on your company's exposure is more important than ever. I recently visited its my cloud 点 com to check my dark net exposure and was surprised by just how much stolen data criminals have at their disposal。 From credentials to cookies to P I I.
Knowing what's putting you in your organization at risk and what to remediate is critical for protecting you and your users from account takeover, session hijacking and in somewhere spy cloud exists to discuss cybercrime with a mission and criminals ability to profit from stone len information with by cloud. You're never in the dark about your company's exposure from third party breaches and info stealer infections. Get your dark net exposure report at spy cloud dot com. Flash dark net dies that's spy cloud dot com flash darkness diaries. Why do you start by tell us your name in what you do?
My name is just of cox on the offer, a of dark wire. I am also a cofounder and journalist. At four or four media .
IT was four or four doing so.
Four or four is a group of four of us, myself, Jason kepler, a manual mayberg and Samantha and we are all former staff members have vices movable the technology site. Uh, unfortunately, vice mates and very poor managerial decisions from the executives. And that company is now bankrupt.
But we left to make our own company where where we we want to continue doing tech investigations. We want to continue telling stories. And how about we do IT in a way where we own the company, you know. So we can not only make journalistic decisions and editorial ones, but we can make business ones as well in the hope we can just keep on doing what we love doing, which is one other thing, stories, verifying information and publishing stuff is in the public interest.
Well, you have you've created quite a name for yourself over the years. I always see your name popping up in, and other books like article by those cards at this or another story here is quoting you and different things. So it's just really well done on your journalism. What this latest project is working on, dark ware. So so I started reading a dark ware and I was just like, oh my god, this is amazing um and I was hope that we could talk about IT.
Of course. I mean, I have been working on this book for three, maybe four years at this point, speaking to essentially every sort of person involves law enforcement is also a lot of very dangerous people. But but I don't think i've ever been more obsessed with a story. I mean, i'm sure of that. I ve never been more obsessed with a story than this one.
Okay, so this is an incredibly nuances story, which is going to fill your head with a lot of questions. I know I did that to me. Let's first start with some context.
I am a criminal, but I make a lot of effort to be private and secure in the first time I made in an effort to have a privacy phone was, after read an article by Joseph, he was using an ipod touch and did all his phone calls over wifi. The main advantage here is that there's no sim card in an ipod touch. IT basically has all the features of an iphone, just no sim card, so that means nobody can seems for you.
But also, sim cards are notorious for beginning out to cell towers and giving fairly accurate location data to cell phone providers. And that's even if your phone is always using A V P N, because sim cards communicate with cell towers using baseball technology, which upgrades completely outside of VPN. So this ipod touch was the main phone that Joseph was using to keep private.
That has been my life for years at this point.
Yeah, you you use that as like a secure phone, right?
Yes, uh, for years I using ipod touch device, and now I ve moved on to an ipad mini because the ipod is no longer supporters. Unfortunate.
when apple stop supporting the ipod touch, I switched over to graphing. O, S, which is a fork of android, is an open source project. IT was a lot more privacy features added in.
And unlike android, they don't send everything I do back to google. My messaging APP of choice is signal, which I can also make phone calls with, because signal is under ending cypher, which means the people at signal can see my messages. Only the receiver of who am chatting with can.
And I do so much more to remain private online. So you can see josef and I, we take our mobile privacy very seriously, and we want the best there is. And then one day, Joseph heard about this new privacy phone called a ARM.
So I call IT an encrypted phone, which is simultaneously a helpful term, but then also not very helpful at all what we really have the terminology for IT.
But yes, it's a combination thing that had a communications up that allows you to send and two gript messages to one another with photos, voice memos and all of that very much like a sign or a modern what sap or a frame or or whatever, right? And IT also was a custom uh, phone Operating system. IT is based on android somewhat, is actually a fork of graphing O S, the privacy focused Operating system. Apparently a orm had also removed all G, P, S functionalities that there would be no way for a law enforcement or google third party to track the location of those devices.
I think the features of a ARM are amazing. I mean, IT took graph in, yes, the phone Operating system I already use, which is considered great already for privacy, and IT made IT even more locked down. what? And the features just kept going like, for instance, a nam had its own little end and encysted ChatApp built in.
But I was in a secret spot. The thing is, there are all these dummy apps on the phone. Like if you look at the phone, IT has tender on there and Candy crushed. They look like Normal apps, but they're just decoys. They didn't really work. And another APP seen on the homework reen was a calculator APP, which worked just fine like a regular calculator, except if you were to open the calculate APP and punch in a certain code that when I would open up the secret anoma chat messaging up IT was hidden beneath a few layers of obligation.
which, hey, that's pretty good if you're having a private conversation and I don't know, an abusive partners, snatch your phone, try to run for your messages or if you're a criminal police office, does this or a border official or something like that. So there's that there's also voice scrambling. So you know how on signal you can send a voice note for one and and very popular missing apps on you could do one way. I'd add something like a high pitch distortion or a low deep distortion to as well. And I would mask what you're real always sounded like .
who is the brainchild behind an ARM who created this thing.
So a ARM was created by someone called afa. I have to be a little bit careful about what I say about them, uh, for reasons they will get into. But they are, from what i've learned, a pretty sort of nerdy tech expert for the criminal underground. They were connected to a very well known criminal code. I can iac, who a one point was australia's most wanted man and this afro character cells, or did cell phones, uh, in the space before eventually deciding, well, i'm gonna go make my like, rather than working underneath ath other sellers and sort of other script phone companies, i'm going to create my own text. Start before the criminal ground .
for the criminal underground. Wait a minute. What like all the features of this phone, they're all fine. None of them are illegal. But if you are specifically making a phone for criminals, knowingly and purposely helping criminals conduct their crimes, now suddenly what afra was doing was illegal. Uh, yes, legally.
it's very, very messy because it's not illegal generally speaking, to sell or use an accurate messaging APP, which is a good thing, to be clear, like that should not be illegal. But a lot of these companies in the eye would say shadier part of the encysted industry.
The thing that differentiates them is that they deliberately facilitate crime as and it's not like signal whose uses would of course include criminals or even apple I message or something just because they are very popular. One of the airlines was the I think he was designed for criminals by criminals, which is just asking for trouble, really. But none had all of those sorts of bells and whistles.
You would expect, you know, wiping the phone, all of that sort of thing. And IT really positioned itself as sort of the royals voice of the encrypted phone industry. If you wanted a super secure device from the company that didn't care, if your criminal, if anything that likes the facts, you are criminal, you can turn to him.
So I learned from the book that this is quite a lucrative underground criminal industry. A num was not the only one here. And you got got to read the book about what happened to all the other encysted phone companies, like each of the competitors have just as wild and crazy of a story of what was going on with a nub.
And Joseph does a great job of giving you a tour of this whole criminal encysted phone industry. But IT bugs me because, like I said, i'm a criminal, but I love having a highly secure phone with the best privacy you can get. So it's a weird line for me that this is even a criminal industry.
It's kind like if someone started a hammer company selling hammer, but I was just selling hammers to criminals, kill people with and I had like features on IT, like non slip handle for when blood gets on IT, or blunt side for smashing goals and fork side for stabbing through stomachs and really is just a hammer that's no different than any other hammer. But IT has the sole intention of being for criminals to cause pain and injury, and the company works exclusively with criminals to find ways to improve IT. Like why? Why not just make a great hammer that the whole world can use? What I make, these secure phones for criminals.
Privacy and security is important to the whole world, not just criminals. Anyway, so a nam was this really sleek, super private phone that you could buy and have ultra cure chats with others. And IT was purpose made for a criminals .
that is basically what annum was pitching itself as to its customers and even to its sellers. IT was saying, your messages will be entered encysted. We can't see what's going on. We won't turn over data to law enforcement of service outside the reach of the five eyes, all of the more sort of marketing and privacy benefits you would expect. Except, of course, um that was in troops and was doing something else in the background.
So what where are they doing?
So is very, very interesting on on on the technical level and what IT is. Anon basically created a ghost contact that was added to every conversation. And I received A A blind carbon copy, A, B, C, C of every message sent across the platform. So when criminal a was talking to criminal b about a cocaine shipment that was secretly being sent off to the norm, and the users were none the wiser, IT was like having a spy in everybody's pockets, in a book pocket, looking over their show they could just .
see into elephant. So while it's true, IT was and and encysted, IT was also ended an encysted directly .
to animal services. Yes, almost is end to end to end encrypt t doesn't other end in the .
so this story just took a ninety degree turn. The phone was not actually as private as IT was advertising itself to be. But hold on tight because we're taking another ninety degree turn right now.
You got ta ask yourself, why was an ARM wanting copies of every message? No, I don't think a nm or F U cared about looking at people's chat. However, F U knew the value of these messages and decided to make a very ideal to let someone see those chats.
And i'm not sure how all the logic went down here. We really don't know how this deal was made. But my best guess is since argue wasn't a stranger to being a criminal himself, and he may have thought this whole encysted phone business is actually illegal and could go very wrong for him at some point, and he needed a plan and really don't know. I mean, I wanted think he was a brilliant business person that just played everyone perfectly but accuse lawyer advised him to make a deal with the F, B, I and let them see the encysted chats. This way the F, B, I would appreciate F, Q and not try to arrest .
him so why not, uh, accused lower health authorities. Would you want to use a norm in your investigations uh in exchange for you know Lillian cy if after uh ever faces um charges right IT became the ultimate argaeus chip essentially.
okay. So that's quite a leap. You know IT takes me a beat to just kind of be like, okay, that's the how the new things go and right it's it's it's a jump .
yeah and this is very quickly done in the book and that's not because i'm sort of glazing over because IT has happened really, really quickly and um that's just a seriously events to happen. Now I don't know if a that was always the plan or something like that or was IT maybe always in the back of afs million. I don't know that, but very, very quickly and norm was put on the table to the F B I back in around uh, twenty eighteen, I think, is when these conversations were happening.
the FBI and australian federal police, yes.
australian federal police for who? For years they've been really time. And by crypt t.
Phones, they probably even more than the FBI in australia. These sorts of phones are incredibly common among organized crime groups. You know you have the italian mafia over there in australia, then using IT.
You want to have the bike gangs like the come cherokee house Angels um they all use these sorts of phones. And for years, if not, you know, more than a decade at this point, the A F, P in particular, has been running into these phones again and again and again. So the idea of a back door in an encysted phone is incredibly attractive to the woman.
What i've been told is that when the A F, P. Agents were told about this possibility and the plan to go ahead. They look like they were kids on Christmas morning.
So a deal was made. The F B I N A F P australian federal police guide access to all the encrypted messages going across an ARM. And this is where I start to have a million questions.
Who that help? Is this F, U person, an undercover cop acting like a fellow criminal, but really working with the feds? What kind of criminal makes deals with the feds like this if these kids discovered his whole business is ruined? Or is F Q A brilliant business person cashing in on both sides of the fence, making money off criminals and federal police at the same time? Maybe he's playing some 4H, S, trying to be a few moves ahead of everyone.
There's a lot of unanswered questions here, but the A, F, P. Were the first to get access to this and they were looking through the logs. And we're like there's nothing here because anna was just a start of company and there are everybody users.
Yet with the product already in the infrastructure in place, IT was time to start marketing the thing. The next plan was figure out how to get these annon phones in the hands of criminals, specifically criminals. And I guess now i'm starting to see what how this phone was purpose made for criminals. Saw the F, B, I and A, F P.
Can see what everyone was doing. So IT starts when after the creator of a ome offers the phones to a particular phones, 还有 a slash drug traffic in australia。 His name is to monico katzer I and he a used to sell fanton secure phones, one of those earlier companies.
And when that company was shut down, he obviously doesn't really have any phones to sell. Well, long behold, here comes after with what looks like it's gonna. The host is new phone on the market. So they he provides some of those phones to cats salty and just starts using them and just starts talking about them and around. I think initially the phones, right, actually just given the free to cotton, and it's almost like a sort of uber technique, silicon valley growth technique, I don't know, just just get out there for free and will will figure out the laws, will figure out the market later. But we just want to get devices into people's hands basically.
Early users were like in these phones, word was getting out about them, and more orders were being made. Chat messages started to show up, and the A, F, P could see what was happening.
at least for australians. The fp, that was relatively real time, instantaneous, you know, they could see that, oh, the camera heroes are talking about beating up this guy. Oh, this bank again is talking about doing a weapons drop off of, like, high calibre assad rifles at this time. In this location, IT was rarely like peeling back. The curtain on these conversations .
was the fp, like actually resting people, or where they just watching, trying to figure what to do. This point I .
have the star, the A F P, as far as I know, is simply collecting the intelligence. There is this massive trade off constantly without this entire story, which is that okay, you have a back door into the phone, but how do you act on that? Do you act on that? And when do you act on the information? Because if you go to lose too quickly, you're going, is gonna become obvious to the criminals that something bad is going on, at least for them.
Yeah, yeah. I found this tension while reading the book quite interesting of, oh my gosh, there there is some crime going on here. We can see that happening.
What do we do that? Do we get push in because you have to have some sort of good reason how you knew that was happening. And if IT was, well, we've got an access to the chat in your phone, then that's gonna rule in the whole company. So they really have to be very careful. And i'm surprised that wasn't just some a of p officer like i'm not gonna careful going going goes stop this drug deal and and just not understand the .
indications of IT yeah he got to the point where the people have spoken to the lawyers, to officials around the words they had to do stuff like basically lie, they had to make up a story whereas like, okay, we are finally going to strike on this drug lab or this drug warehouse or whatever because it's so large and where you have to act.
But we're going to write the intelligence in such a way that looks like it's coming from an enforcement or a source. So there's going to be no mention of a ARM, no mention of the back door. And you know from a law force perspective, that's great, you know, okay, we we manage to get the drugs and arrest of people of whatever while without revealing uh you know the the secrets about the norm. On the flip side, there is a justice issue there. You know that's basically parallel construction um is very complicated to gets rain you want but do you think the civil libitina arians would be a little bit guest sort of the trade officers were being later on the daily basis?
I think everyone's a guest to the whole .
story yeah yeah because .
here's a situation with the federal police are lying on the record about where'd get no intelligence from are the citizens of that country OK with that tear in the U. S. During court, your act to swear that you are telling the truth.
The cops weren't telling the truth here, or I guess, not yet telling the truth. We learn later how they did get this information, but the evidence in these earlier cases did not mention a ARM. But additionally, they were working with this criminal afo to get these messages.
And I call him a criminal. Because if someone makes an APP exclusively for criminals to conduct crimes with, then historically, that's criminal behavior. So who's ago and when did the police start making business deals with criminals? Is there proper oversight here?
Is this within best practices for the feds? Point to the policy that allows this. This just isn't. Sit right with me. And you might say to me, jack, the ends justify the means if all these results, and I take down of a lot of criminals, and it's OK for them to lie and do back ali deals with criminals, really.
What about fast and the furious? This was a real Operation done by the eighty of alcohol to back on firearms, where they set up weapons deals with criminals so they could track where these weapons are going, and ultimately tried to arrest a bunch weapons sellers. Yeah, well, IT all went wrong.
The A, T, F. Made weapons deals, but lost track of the guns that were sold. They didn't make significant arrests and basically armed the very criminals they were trying to find and arrest.
This ultimately resulted in a border patrol agent getting killed. And at the scene of the crime was one of the guns the A, T, F, sold to criminals. The ends did not justify the means here.
The fast and the furious Operation was a big mishap, and IT showed how the A T, F was Operating without proper strategy or oversight, or following policies put in place. What is the deal? Did they did FBI take ownership of IT? Or how did they IT was a licensing .
like licensing and Normal stuff is is uh so the the deal itself is between after u and U S. Authorities and got paid something like a hundred twenty thousand dollars and then sixty thousand dollars for a travel expenses I think is how is phrase in some of the the documents? But anon basically became N F B I tech company from what I ve been told from people with direct involvement.
You know, the F B, I was picking up the bill. They were paying for infrastructure. They were paying for hardware, android hardware, for the phones, uh, for the APP to be flashed on.
They were, they were running a tech company. And I think that's just the crazy st thing here. And beyond that, they were running a tech company, for criminals。
Yeah in in, in its fascinating to that afro is somehow able to control the company in a way that all the developers and suppliers and shippers and everyone, even the distributors, had no idea that the FBI or A F P was involved, right, or even that there was a man in the middle. I mean, was was the kind of the thoughts going on in the developers head, did they know that they were building men in the middle, encrypted and encysted? Or what was, what did they think?
So yeah, I ve spoken to people who actually code at the APP and basically made the phone. And these were completely ordinary developers. You know, when I spoke to who I call at IT in the book, I used a different name just to protect their identity.
But they found, like a financing gig online about the secure communications APP. They get involved and they're doing Normal coding like theyve done a million times before for an android APP. And what they told is that we make this APP and we sell IT to businesses. We sell to CoOperations to protect their communications. And as part of that um companies like to be able to order IT the their messages, you know and that's very common and banking, very common and financial of that sort of thing for legal reasons.
Yeah I found that part to be interesting. I didn't realize how why. So at the other day, I was looking to see if um google has any sort of end and encysted in their chats and I didn't think they did. But they're like that we do like shoot, sign me up and it's like, well, what we have is for businesses, for enterprise. And what the way we have is set up is that the admin of the account can see all the messages that your users are sending encysted.
And I was like, what? Hold on a second? Why would you have a man in the middle of an encysted thing? And then I read your book and I was like, oh, this is more common than I realized where company ties do like for instance, I think you mentioned um you know federal federal agencies have to be able to pull up any communications, emails, chats, messages and stuff in case there's indictments or spas.
What did what was talked about federally or even state agencies, at least in the U. S. Here, this stuff has to be archived.
And if it's ending encrypted, you can archive IT in a proper way. So there is a reason to get in and take a look. I don't know. This kind of just surprise me.
Yeah I mean, customs and border protection part of D H S. They use weaker the encysted apps that many people be familiar with, but they use an enterprise or government version, which yes, it's enrica, has that extra archiving function and the developers of a norm, that's what they thought they were building. They thought they were building a communications platform for businesses to, yes, talk somewhat security, but have the messages archive.
So then, for whatever reason, the administrator can go through them at a later date. That's what they thought they were doing. What they weren't told was that the fines are being sold to criminals. And the archiving features actually for the F B I F, uh, left that the out when telling the developers about that.
And I mean, just very briefly on that, like the compart, the compart mentalizing, the F F U did, I think is very interesting, as in like there were the people designing the APP, and they were sort of in their own silo that within people making the custom fork of graphing O S, the android Operating system, and there was those people. And then somewhere else there were the you know the criminal sellers on the ground and like these groups, not really communicated with one another. And i'm surprised I didn't leak to be perfect honesty and genuinely surprised but somehow um I I must stay a secret, at least for a long time.
Too many secrets. C to astronomy. I mean, think about IT. The criminals think they are the ones being the most secretive here. They've got these super private anoma phones, which you need a pint unlock and then go through a dummy, calculate APP to punch you in the secret code to get into the chat apps.
They are end to end encrypted right then they're doing things like disguising their voice and having disappearing messages and being super secretive about their crimes, trusting a num with all their secrets. But then there's afghans who is secretly scooping up all these messages and liked his developers of who these customers are. And then there's the FBI and A F P who are secretly reading them all and secretly making business deals with afc.
U. I mean, did you know that the FBI was Operating a tech startup, which was a phone purposely built for criminals to use to message each other? Secrets work up from you in the story too? Well, criminals had no idea they were being played. So an ARM phones just kept spreading. They ended up making their way to some criminals in europe, and things really started to heat up there.
The phone start popping up in europe. And that's when broadly, sort of the swedish police get involved. And then also the dutch, they are the two main in european agencies.
That first come forward because I simply whether phones are ending up and obviously the A F P doesn't really have jurisdiction over sweden or or or the nevels and the F B I A, although they are reading the messages by this points, uh they know in english for a start. And the F B, I can't really go over and start arresting people and then, you know, nor should they. So they decide to share some of the intelligence with their swedish and their dutch counterpart. And he starts to mirror what's going on in australia with you know more intelligence gathering in the rest hair and the rest there. But it's still very much under wraps even though more and more cops, some crazy things started .
happening with the on. At this point, IT takes more and more ninety degree turns. I'm not even going to get into what happened europe or south america, turkey.
I'll simply say that there are a few criminals that love this and non phones so much that they try to purchase otherness of that company and eventually to started calling themselves the CEO of a ARM, which, when a major underground criminal is saying he's the CEO of an IT, really legitimizes the phone for other criminals to want to buy IT. So the anoma phones were starting to grow wings and take on a life of their own. In europe.
At this point, i've read, I think, tens, if not hundreds of thousands of and all messages and messages from other provides as well. And what's emerges for reading those is that a lot of people whose sell these encysted phones in a particular market or territory, they treat IT like having a drug territory like in the same way that somebody may be a the wholesale distributor for um you know a certain part of sweden or maybe uh and for or something like that, these phone dealers treat their product in the same sort of way.
And so I I want to shift gears here to the FBI. So so I got a lot of questions about what the F, B, I to. And here, first of all, F, I handles internal threats to the united states. They're not A, C, I, A, which is doing international investigations. So I don't even understand why the FBI would be looking at foreign passage is in the first place.
Yeah, I think this is something that a lots of people reading the book have an issue with. basically. I think that only way to put in, which is like, why is this U. S. Law enforcement agency intercepting and reading messages from all over the world.
And the best answer I have is that what is too this sort of the legal one, which is that know the four amended only protects people on american soil, right, where you have to get a surge and seizure warrant to go through communications or a wide APP order or whatever, right not to get too technical. Um the F B I does not lead up for overseas um and that's basically sort of the loophole that they use where they were able to go through all of the data. The second one is like sort of a how they see themselves and maybe uh how they see the the ethical obligation as well.
But like the prosecutors i've spoken to who involved in this case, they just simply see this as a good thing and they want to go out and they want to shut down all of these criminal gangs. They want to intercept them uh I think that there are valued questions about you know national sovereignty and all that sort of thing um but that is what the FBI set out to do. They set out to wide up the world essentially, and they were very, very successful lather.
There's just so many questions I have at this point now, many phones in the U. S. So the F, B, I couldn't look at U. S. Citizens chats, even if they want IT.
But the FBI was heavily involved with an ARM creating the start up, basically funding IT, creating a infrastructure, actively monitoring the messages and IT just makes me wonder, have they solved all the cases in the U. S. already? Because to start a tech company and collecting and analyzing and reporting intelligence so that you could give IT to other countries, that takes a lot of time and resources. So whose idea was IT to divert FBI resources to focus on stopping crimes in sweden, in australia?
I mean, IT IT, it's partly they are doing IT because they can they can change these communications. They can yes, they can't go arrest people themselves, but then they can provide the intelligence to foreign partners. I mean, is is sort of a overused cliche at this point in the idea of amErica being the world police or whatever.
But there is this, there's an element of actio type here, and that the F, B, I went out and they collect all these messes all around the world, even though they months of what was going on. america. This is sort of the future of policing there were in now.
And that wasn't really debate about IT. IT was just like one day or several days over the past a few years, police have just decided they're going to hack or other ways to intercept communications, uh, all around the world basically. And we didn't really get a chance to talk about that as a society, about whether that something we want maybe IT. Turns out we do like, I don't know, but we can have a conversation unless we know what's going on. And that's kind of while hoping to .
do with this book, pause and consider this. The F, P. S fundamental Mandate is to protect and defend the nation from threats. Defend, however, in this story, they've gone on the office in the name of defense. And this difference is worth noticing.
I mean, imagine you're defending yourself in some legal battle and you're worry you might lose because of some surprise thing the opposition might bring up. So to defend yourself Better, you decide to break into the other lawyers office and steal all their notes that they have on the case, or hacked in to their phones and see their chat messages, all so you can Better defend yourself. Well, this tactic would be unequipped unethical.
Yet the fb strategy here is to penetrate private chats in pursuit of criminal activity. It's crossing that boundary from passive monitoring to active intrusion. And I think it's important to be aware when that boundary gets crossed because we never save them cross IT, since it's always done in the shadows.
If the F, G, I were to cross that boundary in the physical world, IT would be a kin to them secretly breaking into thousands of homes, rummaging ing through personal belongings, because they're trying to detect crime. This wouldn't be acceptable. So why then should our digital lives be subject to a lower standard of privacy?
I guess the F B I uses all kinds of Spike are though, to cross that threshold all the time, like wired tapping in planting bugs. They're always covertly reaching in the someone's communication and taking IT. But I think what's different about this story is the mass surveilLance aspect to IT.
All messages for all users were being collected and stored. And maybe IT wasn't stored in the FBI database exactly, but the FBI was funding this company who was collecting at all. I remember when the snowden revelations came out, the N S A N G C H Q were trying to collect massive amounts of data flowing over the internet.
Not targeting a specific person, just grabs everything, which means a lot of dawn criminals were getting their data analyzed. I wonder, is that offensive as well? It's mass spying at least.
And everyone don't approve of governments doing mass buying on their citizens. But this is a crazy ethical delima. Because what if the mass spying is just on the criminals.
I think is something the cryptographers and privacy experts exception in the book were worried about, which is the some of them are less worried about the specific case of the norm, but some are, to be clear. But they're more worried about, well, what happens now if we have a network is ninety percent criminal and ten percent Normal users. Is that a fat target?
I don't know what happens when IT moves to fifty, fifty, you know. And there's a really good quote in there from Matthew Green in the crypto logic. And he says, well, maybe fifty percent of the criminals on this network are doing really, really bad stuff, like trafficking or whatever.
And then fifty percent are doing like, I don't know, copyright infringing cement of song lro s something that I don't think many people are really care about in the eyes of law. Forcing is that fat target. And that's the discussion we're not having, and we need to have that as quickly as possible because i've always no enforcement to just gonna hand.
Do IT people sometimes say to me when we're talking about government's surveilling that you've got nothing to hide and they aren't worried about IT? Well, with those people are really saying is that they're always going to comply with the government no matter what. They're never going to have dissenting views or protest.
And honestly, i've never met anyone who one hundred percent agrees with the government no matter of leadership. It's important that we preserve our freedom to have opposing views without the government watching us. Because the thing is, if we're being watched, IT changes our actions.
I mean, gosh, in this story, the themselves has to hide, and they can spy on people in the U. S. Without proper warrants and stuff. But they were circumventing this rule by providing intelligence to other countries. And in those countries is providing intelligence back to the F.
B, I. Yeah, yeah. It's, it's a worry, not a big worry. The stones, in this case, he was like, even though the FBI can look at phones in america, the A, S, P, agreed to keep an eye on the ones on american soil for threat to life.
And you know, on one hand, you could say that, well, it's good. The F, P, were monitoring that, so nobody got hurt. Hopefully on the other end, well, why didn't the F, B, I go warn to do themselves?
So we're gonna take a quick ad break, but stay with us because, well, clearly you can see there's a ticking time bomb go on at this point. This episode, sponsored by a threat locker, ran somewhere supply chain attacks and zero day exploit. Tes can strike without warning, leaving your businesses sensitive data and digital assets vulnerable.
But imagine a world where your cyber er security strategy could prevent these threats that the power of threat locker, zero trust and point protection platform robot cyber security is not negotiable to safeguard organizations from cyber thread locker implements a proactive, denied by default approach to cybersecurity, blocking every action process and user unless specifically authorized by your team. This least privilege strategy mitigates the exploitation of trusted applications and ensures twenty four, seven, three, sixty five protection of your organza. The core of third locker is its protect sweet, including application allow, listing, ring fencing and network control.
Additional tools like the threat locker, detect E D R, storage control, elevation control and configuration ation manager enhancer cybersecurity posture, and streamline internal IT and security Operations. To learn more about how threat locker can help mitigate unknown threats in your digital environment and allowing your organization with respect and complained frameworks, visit thread locker dot com. That's threat locker dot com. The unarm phones were getting picked up by some criminals in europe who were taking them to dubai .
to try to sell on air of the phones in dubai. And you know part of the U A. And the U. E.
Is very interesting because it's one of the very few places that you're not allows to just go around and start starting an encysted phone or encrypt to APP. If IT is not approved by the government, you can get into a lot of trouble. You, I guess, of in the same way, like the russian federation.
why? Why is encryption a problem there?
IT has to be approved by the government, is basically a combination of a censorship and a surveilLance sort of posture. Whether if you are selling and encrypt t APP that the local authorities and national authorities do not approve of, you are not allow to do that. And the reason being is that what they want to be to access that and h somebody running round selling a norm phone is not going to get on the good side.
See, it's not completely out of the question for your government to ban encryption to force the people of the country to use certain apps so they can see into IT. This, I think, is a huge violation of our privacy. Luckily, in the united states, we have the fourth amendment of the constitution, which states are really the whole thing for you.
The right of the people to be secure in their person's houses, papers and effects against unreasonable searches and seizure shall not be violated, and no warrants shall issue, but upon probable cause, supported by author affirmation, and particularly describing the place to be searched in the person or things to be seized, the forth amendment is needed to maintain a baLance between national security interests and individual rights. It's a tool to make sure that the government actions are subject to oversight and grounded. And if we eliminate that protection, IT creates a really dangerous power dynamic and a slippery slope towards the government that could abuse its power with no accountability.
If the U. S. Government did some kind of mass surveilLance, I was searching through all that data without a warrant, IT seems to me that would be indirect violation of the U. S. constitution.
And yet here's a situation where the FBI was running a tech start up with the entire goal to be snooping on other user chats, watching every message to see if there was criminal activity. There's no targeted search here. No individual warns were being made at this point.
They were analyzing all the chat messages going through an ARM. Is this in violation of the fall commitment? I can make a case that I was and the F, B, I had that in their head, too. So they were trying hard not to peak into any americans messages. The data was available in an arms database, but they had to program their system to only .
show them foreign chat rooms. FBI was leading the anonyme messages in. I've obtained screen shots of what the F, B, I interface looked like.
So I feel like, I feel like I can put myself in the heads of some of these FBI agent, because i've also read at one of these messages as well. right? And the system itself is called holler.
I bot, you logged in. Uh, initially I was just from the Sandy ago F. B.
I. Field office, but then they made a remote as well for the european partner. Also because of cove IT h people couldn't go to the office as much.
You log in and the source of Green and black uh interface and you can click on an individual and orm user and IT will show sort of a conStellation of all of their contact. We'll be a circle in the middle enough, a circle of the person they spoke to and an a circle which shows all of the group chat. You can then zero in on those is always like a maltin sort interface.
And then once you go to a specific user, you can see all of their messages, you can see all of their photos. And rather handy, there was also A I powered summary ies of what was being spoken about powers, at least some way by amazon. B. F, I used to amazon capability there. So you can look on the right side of the screen and it's like Jerry is talking about a cocaine deal, whatever is.
And sometimes it's that lunt, which was just a always hilarious to me when IT gets to the point where there there are millions and then tens of millions of messages, the fb, I had to turn to some of these AI capabilities because otherwise they are gonna be swiming data. And by the ends they were absolutely swimming data. There was a real danger. But if they did not analyze every single message, but what would happen if the one message about a Derek got and somebody died, that was a constant threat, and IT really, really wrapped up as a non became especially .
more popular. This tool that they were using was IT, developed by anoma or developed by FBI holo.
Ibot was developed by FBI computer scientists, who was made in house as basically like the surveilLance interface of .
a nom IT sounds pretty advances to be able to have this graphical view of whose connected to who, and then also use A I to search force. Because a lot of the criminals are using code words for for different drug names and all these kind of stuff, thinking they're Sparking the police but they're able to find all that.
Yeah and I mean, if you think about IT like the imagine a Normal wot like L A or something and it's one guy talking to another guy in a Normal phone and they're talking about a drug deal. And if you're the F B I, whoever, you have to figure out who these people are and that might be tRicky.
You know as you say, maybe they are using code names, maybe they are using sums, and then you go about, you maybe a phone location data, you figure out how they are, whatever. Now imagine doing that for something like twelve thousand people in one hundred and fifty different countries. It's like, I almost can't picture the task in front of them and that's why they had to turn to these pretty sophisticated or systems figuring out not just what people are saying, but who that held these people leaving are.
And they would do that and then even put, you know, the theory, typical graphs on the wall in the F, B I with a the the layouts of different criminal organza. And in some cases, the FBI doesn't even know who these people are. At first they just like, well, we have a new crime syndicate on the platform. This start mapping out how they are related to one another.
So you said, you know, we're looking for that started of life or what was what was like really what they were like. Let's not let this slip through and really trying to .
focus on yeah so as well as the drug trafficking, the main thing that flows across the norm where what the F B I was threat to life and this is where um a criminal organization or just an individual criminal, we want to harm, torture or in many cases kill somebody else and this happened across the norm constantly to the point where one of the F B I agents who was reading the anno messages at first.
His task was just to go through every single image that was sent across the platform and often these were weapons or locations or targets and the way I was described to me is that is trying to figure out a puzzle basically as quickly as possible. You have to take all these desperate pieces of information and maybe you only have a photo of, uh, a weapon. So that indicates there's probably going to be violence here.
Or maybe you only have a photo of the location is like what something in's gna happen there. And the fb, I would have to very, very quickly, as best as I could figure out this puzzle, give information to uh, foreign authorities who can then act on IT and then maybe save people or or maybe not. I I don't think he was always successful, but they did save lives in the process, uh, as well.
It's gotta be really complex because when you when you just see two criminals talk to each other over message, they're gonna easily say, i'm gona kill you, man is necessarily mean it's gona kill them but it's just one at least this way our lingo is and and then the opposite is when you're saying, okay, listen, we really need you know of this one person. There's also like all kinds of um you know coded messages in there just be like right minus one this guy and like minus one what is minus one me now means get kill them right so you have to like decode this this is that doesn't that must be incredibly difficult yeah there's a lot of postering in there .
for the enorme messages i've read where there are people doing exactly that like i'm gonna ill and then you'll come across the messages where like they are talking specifically about getting a getaway or to drive away from the restaurant after they've killed somebody. Then they need to rent an airbnb to hide the assessment like when IT starts to get specific granular at least to me that's when it's like, oh, okay, we need to actually take this seriously and that's what you know the switch thorium did the dutch as well and especially .
the FBI yeah and it's also wild because typically what we're talking when we're looking at the or when no one I was read in the bucket seemed like this is criminal on criminal gang on game activity, right? And so trying to save the life of a the criminal is sometimes a strange um you know moral situation you're dealing with here.
Yeah IT puts the fb N A complicated ethical spot, and he puts the agents, the foreign agencies, in the same spot as well. What's started to happen with the F, B, I or his partners was intersect communications about a threat to life. The authorities will act on that. You know, they would somehow stop the killing, and that could be in various ways.
But then what would happen would be that the criminals will continue talking, and they would go, uh, how did the authorities know we were going to kill this guy? And they wouldn't assume that was a norm, they would assume there was a moll or ratten the organization, and then they were trying to kill that purse, said, then the affair has another threat to life. And they almost became like this endless cycle spiral where IT started to become exceptional. Difficult for the F, B, I to maintain tempo is is the way they described IT.
There are so many ethical and moral dilema here. I mean, just to imagine A A I tool that out there scouring messages, looking for a threats to life. But the tool has to be trained to ignore IT if it's an american on phones.
As I found through reporting this book, they absolutely landed on american soil. There were animal phones being used inside united states. There was a plan to start phone for the FBI to start reading those messages.
but IT was very difficult for them to figure out what to do with all this information .
they collected. They are basically stonewall in being able to look at us communications that just didn't seem to be the appetite to go after people inside the states. Even though the prosecutors in the agents on the case very, very much wanted to.
They were ready to do IT. They were collaborating with a field office in los Angeles as well. Um he was just a matter of basically pulling the switch by higher ups of the D. R. J. 嗯, shut that down essentially.
I mean, what what these chats look like, does the F, B, I go to congress or what and say, like, hey, we've got this. Okay, I sit down because I got some crazy story to tell you. We've got this.
We've got this massive surveilLance tool that we somehow bought from some guy, right? It's now we now have like you into like the whole criminal world here in the us. And you know a large portion of IT, um we would like to do a math arrest because we can see this and but we don't have the a the warrant. We need to help like what does that do you have any understanding of what those conversations were like?
yes. So what happens when I was first approved um for the F B I to gain access to the messages in jamo with that most drug prosecutors in sand ago in a specific meeting I describe they would like, no this is a ridiculous idea, you can do this and then um on top of that .
they were like, well, don't even look at the U. S chats, right? Like just look the other way because we don't have a approval to even look .
at IT yes exactly. They were like please don't look at the U. S. messages.
We will figure out later and what happens was was that, uh, the prosecutions on that, they they sends the request to a specific pounds of the D J. Called the office of enforcement Operations. And there are the ones you basically approve every White top.
If you want a White tap in the U. S, they have to approve IT and the prosecutor is on the animal cases sent that and O, E, O just settling IT for month of months and month. That was clearly like this device between sort of the cowboys on the anne case and then like the the more senior people in D O J who just like we're absolutely not um approving this.
And a nm obviously grew to a massive size even without there. But IT could have grown even bigger, potentially even more. Disastrous consequences .
you have but like we've been talking, produce so many ethical dilema within the enforcement of world. Do we need a wiretap for this and all this kind of stuff, what's aloud and what's not allowed? And I just like screw IT, we're gonna get all the data and will figure out what's allowed later IT seems weird to go that direction.
Yeah I I absolutely. There should be a debate around whether secretly running attack company should be allowed. There should be a debate on whether we want to be able to hack into entire team communications providers.
Maybe the end result that conversations that we as a society, you are OK with the tradeoff. But I don't think ordinary members of the public, one, first of even know this is basically happening. The second of all, aren't aware of what those trade or see and are, how can we even have that conversation when this is basically done in the shadows and then everybody moves on?
yeah. And I also just realized how if the F B I is running a tech company that is communication platform, which is facilitating ating, the murder and drug deal, like are they responsible for? Were the ones who made this communication possible? Where are the ones who put the phone in your hand to make this even that happen? There is there is some responsibility there.
I mean, there's no two ways about IT the FBI facilitator crime with the development and the ongoing maintenance and the secret running of the norm. The FBI was a tech backbone of organized crime. Now, yes, of course, they also have the surveilLance capability as well, but they were selling a product to criminals and the criminals making great use of IT.
It's like the ends justify the means in some way.
I think that is how people who work in the Operation um would phrase IT. And as for the ethical responsibility from everybody I ve spoken to, they did take the ethical consideration seriously like we are running the communications platform and that's why if a murder does flow across the chats, we need to respond to IT aggressively and uh, quickly. Now that didn't always work out, unfortunately um but that was the approach they were coming from. By the end of the day, those messages are still on F, B, I chat up.
Should I I think about afro again? He was making a phone for criminals, right? Like he was working with criminals, listening to their requests and adding in features like a remote ability.
So because africa was making this for criminals, IT meant he was a criminal, clearly, right? Yet IT was the FBI who was the true owners of this company. So what does that make the FBI if they were making something purposely for criminals to use the implications of the story? Just keep going and going.
I've tellyou. I have like a million question. I just love this book. June seven, two thousand and twenty one.
yes. What happens on this day? sure. So the F, B, I. And his foreign partners, they decide on the date june seven, twenty twenty one. The reason for that is that the country there was sort of part of the technical infrastructure livvy ia um they called order was running out. But basically an army which is getting too unwhipped IT was starting to get out of the fbs control.
Sellers were pushing into countries, uh as they wished every time the FBI arsenal resources to monitor the messagers, which was eventually like a hundred and first F B I agents and total than more messagers came and they to ask for more resources, there had to be an end point. And there was basically the date that was picked. Before I went over the age, I spoke to multiple law enforcement specials who were part of that day, and the pressure and the stress they felt was incredible.
The way was set up was that I was almost a global line of dominoes starting in australia. And they would do their arrests first. IT would then move over to europe and then they would do their arrests.
And then eventually, when people woke up uh, on the west coast in sunday ago, the FBI would come forward and they would take credit for running a ARM. IT was the single largest law enforcement action in any one day, something like ten thousand police officers were involved in that one day in this world spanning relay race. Domino track of activity.
Good morning. I am Randy growth man on the acting united states atterley for the southern district, california. welcome. Thank you for being here. We are here today to announce the unceasing of a federal indictment by a grand jury in the southern district of california, which charges seventeen foreign nationals in facilitating drug trafficking, money launder ing and obstruction of justice.
This is part of a worldwide law enforcement Operation that has resulted in hundreds of arrest for drug trafficking, money launder ing, firearms violations and crimes of violence. These international arrests and the U. S.
Charges were possible because of a Sandy ago waste FBI investigation. Like none other in history, this investigation, called Operation trojan shield, shine a light into the shadow industry of harden encrypted devices. For the first time, the FBI developed and Operated its own harden encrypted device company called anam A N O M as release.
Our entitled criminal organizations and the individual defendants that we have charged purchased and distributed anon devices in an effort to secretly plan and execute their crimes. In fact, animal distributors, administrators and agents had so much confident cy in the secrecy of their devices that they openly marked them to other potential users as designed by criminals, for criminals. But the devices were actually Operated by the FBI.
The worldwide implications of this investigation are staggering. In total, the criminal sold more than twelve thousand and and encysted devices and services to more than three hundred criminal syndicate Operating in over one hundred different countries. This was an unprecedented Operation in terms of its massive scale, innovative strategy, international coordination and investigative achievement. Operation trojan shield has shadow any confidence criminals may have through the use of harden encrypted devices.
shattered any confidence that criminals may have in the use of encrypted devices. I'm not sure this is a good take because what about me who just wants a hardened encysted device for, you know, privacy and security?
Yeah, if you want ordinary person and you trying to figure out whether up is legitimate or not, I can be really, really hard to tell. Yes, you'd look at the owners like all of that sort of thing. And you know maybe some researchers dig through the code or whatever IT is even beyond that, like you, even beyond looking for specific answers, is just that.
We know the F, B, I S. Prepare red to do IT. Now, which changes the conversation.
Someone even asked the FBI at the press breathing thing about this, is this something you can .
replicate and do we get so who knows?
right? This will not lead all of our criminals. Guessing of what company out there is actually a true secure company in which is run by potentially the government. So we obviously have the take technical capability ah and obviously the international partners ah to work these types of cases in the future.
I basically believe the FBI is absolutely expLoring more of this. To get some of the information in the book, I snuck k IT into a long enforcement of conference and vancouver, where two of the agents were talking. And towards the end of that talk, one of them said they look forward to like what the next version of Operation trojan shields, which the animal Operation, looks like.
That's not an agency saying, okay, job well done this or go home. That's an agency looking for an even bigger thing to do next. And as well as an ARM, there was the sky hack.
There was the enco chat hack as well. Absolutely, law enforcement are continuing to push down this route. I mean, some of the police officers I ve been spoke to told me that the dutch authorities told me we are doing this right now.
This is why I love john p. So much. He's speak in the law enforcement conferences to get the story. We skipped over so much of the book. I purposely left out some of my favorite parts of the book just so you can enjoy IT still, this story goes deeper and deeper and deeper, and so you should do yourself a favor and go read dark wire by Joseph X.
A big thank you to Joseph cox for sharing the story with us. You can find a link to his book dark wire and the shown notes. Again, it's highly recommended. This episode is created by me, the bit bomb ler jackey sider. Our editor is the silicon source er trest and leger mixing is done by prox soner intermix c is done by the mysterious breakfast matter singer. One time I went into a clients data center to do some work on their, and I found a computer that was so old, its I P address was one, just the number one. This is darkness diaries.
